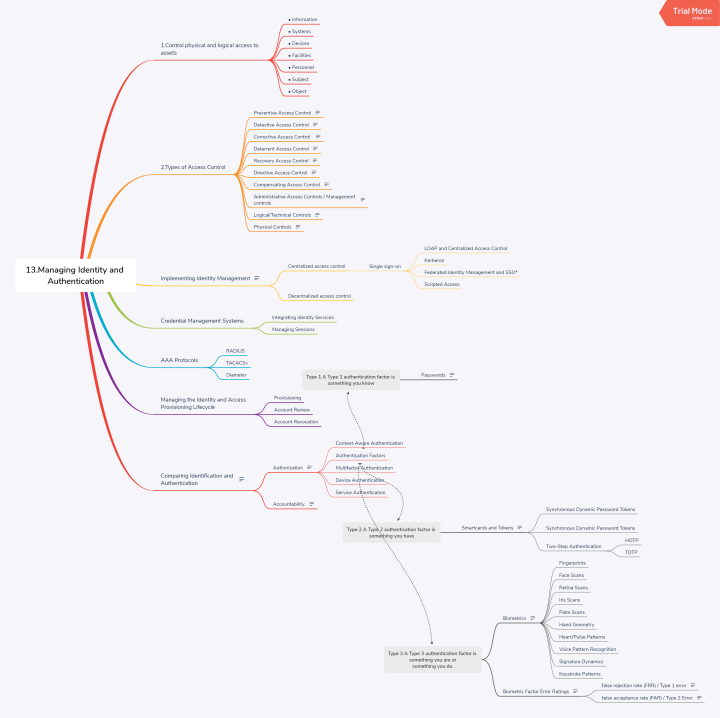
1. AUTHENTICATION METHODS
- There are three basic authentication methods:
- Type 1 (something you know)
- Type 2 (something you have), and
- Type 3 (something you are).
- A fourth type of authentication is some place you are.
- Type 2 authentication (something you have) requires that users possess something, such as a token, which proves they are an authenticated user.
- Synchronous dynamic tokens use time or counters to synchronize a displayed token code with the code expected by the authentication server (AS).
- Asynchronous dynamic tokens are not synchronized with a central server. The most common variety is challenge-response tokens.
- Type 3 authentication (something you are) is biometrics, which uses physical characteristics as a means of identification or authentication.
- Three metrics are used to judge biometric accuracy: the false reject rate (FRR), the false accept rate (FAR), and the crossover error rate (CER).
- False rejections are also called a Type I error. When the data points are lowered, the organization risks an increase in the false acceptance rate. The organization risks an unauthorized user gaining access. This type of error is also called a Type II error.
- A false accept is worse than a false reject because most organizations would prefer to reject authentic subjects to accepting impostors. FARs (Type II errors) are worse than FRRs (Type I errors). Two is greater than one, which will help you remember that FAR is Type II, which is worse than Type I (FRRs).
- The CER describes the point where the FRR and FAR are equal. CER is also known as the equal error rate (EER). The CER describes the overall accuracy of a biometric system.
- Retina scans are rarely used because of health risks and privacy issues. Alternatives should be considered for biometric controls that risk exchange of bodily fluid or raise legitimate privacy concerns.
2. ACCESS CONTROL TECHNOLOGIES
- Centralized access control concentrates access control in one logical point for a system or organization.
- Centralized access control can be used to provide single sign-on (SSO), where a subject may authenticate once, then access multiple systems. Centralized access control can centrally provide the three As of access control: authentication, authorization, and accountability.
- Decentralized access control allows IT administration to occur closer to the mission and operations of the organization.
- Decentralized access control is also called distributed access control. FIdM may use OpenID or SAML (security association markup language). SAML is an XML-based framework for exchanging security information, including authentication data.
- LDAP is an application layer protocol that uses port 389 via TCP or user datagram protocol (UDP).
- SESAME stands for secure European system for applications in a multivendor environment, an SSO system that supports heterogeneous environments.
3. ACCESS CONTROL PROTOCOLS AND FRAMEWORKS
- The remote authentication dial in user service (RADIUS) protocol is a third-party authentication system. RADIUS is described in RFCs 2865 and 2866, and it uses the UDP ports 1812 (authentication) and 1813 (accounting).
- Diameter is RADIUS’ successor, designed to provide an improved AAA framework. RADIUS provides limited accountability and has problems with flexibility, scalability, reliability, and security; therefore, Diameter is more flexible.
- The terminal access controller access control system (TACACS) is a centralized access control system that requires users to send an ID and static (reusable) password for authentication.
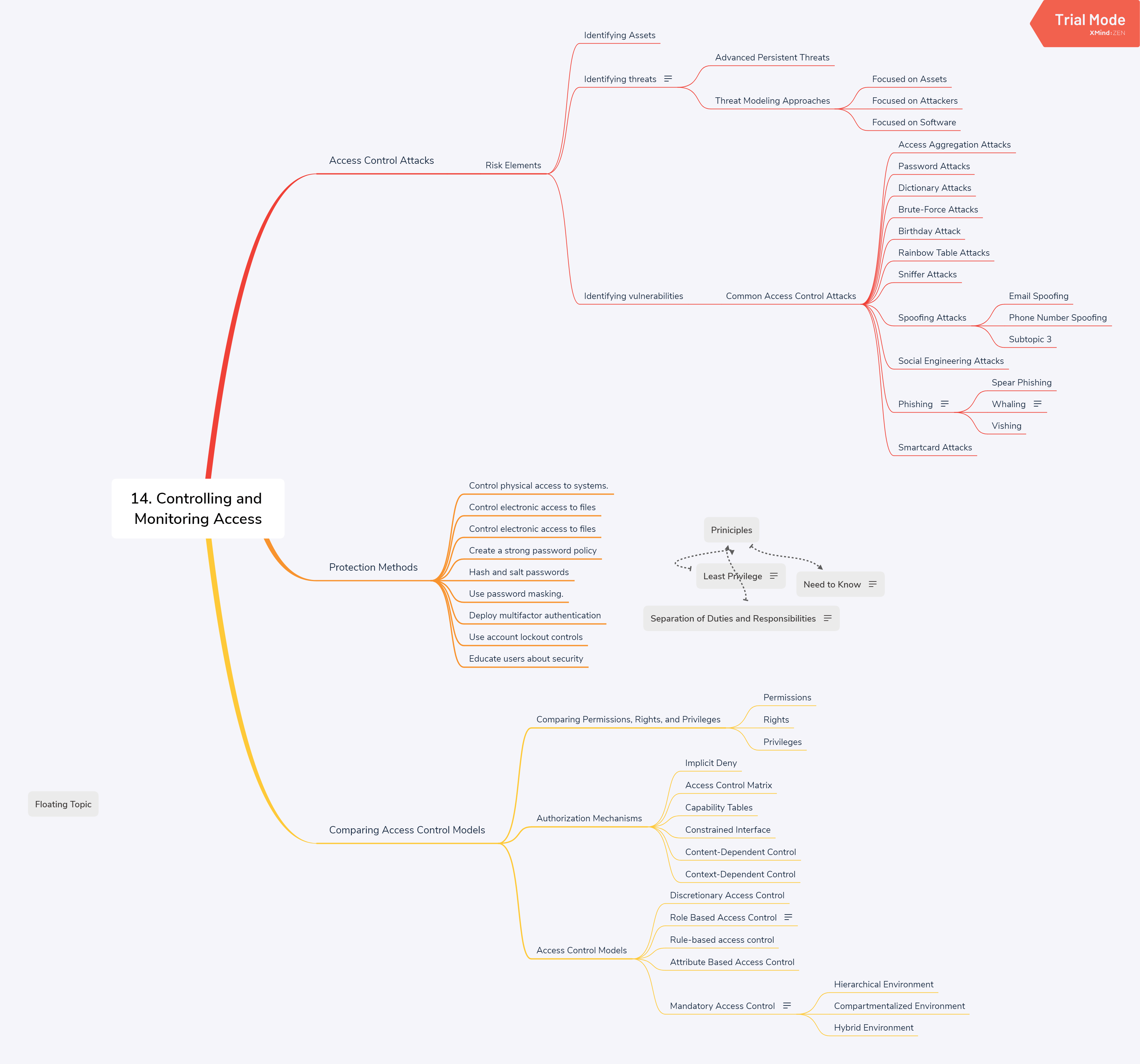
4. ACCESS CONTROL MODELS
- the primary models are discretionary access control (DAC), mandatory access control (MAC), and non-discretionary access control [Role-based access control (RBAC)].
- Task-based access control is another non-discretionary access control model related to RBAC.
- Content-dependent and context-dependent access controls are not full-fledged access control methods in their own right as MAC and DAC are, but they typically play a defense-in-depth supporting role. They may be added as an additional control, typically to DAC systems.

Leave a comment