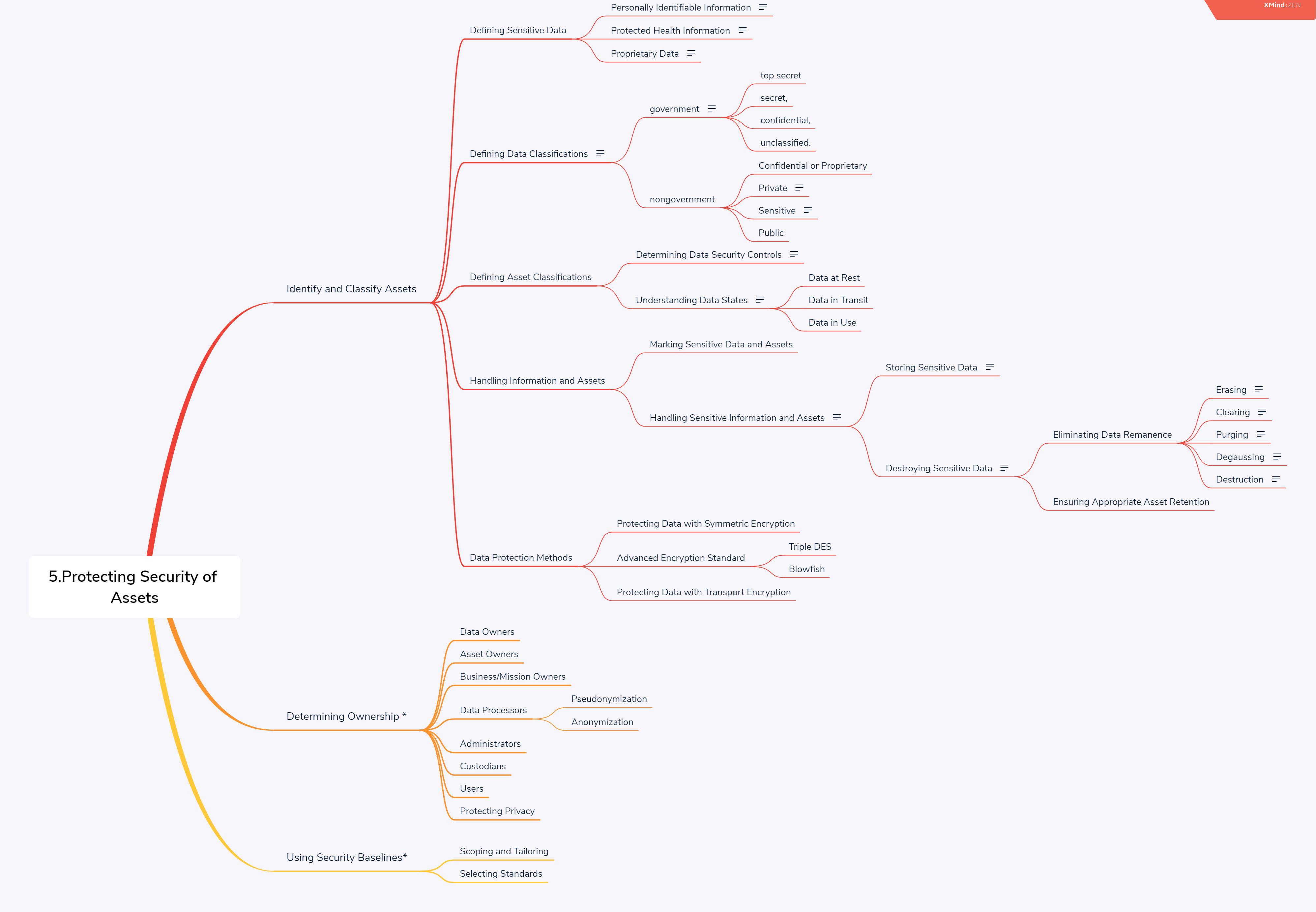
Types of Sensitive Data:
- Personally Identifiable Information
- Protected Health Information
- Proprietary Data
Classifying Data:
- The day-to-day management of access control requires management of label
- These formal mechanisms are typically used to protect highly sensitive data.
- Categorization – Process of determining the impact of loss of CIA of information to an organization
Government:
- “Top Secret” – grave damage to national security.
- “Secret” – cause serious damage to national security.
- “Confidential” – damage to national security
- “Unclassified” – Public release from Govt officials.
Private sector:
- “confidential (or proprietary),” – grave damage to private organizations.
- “private,” – cause serious damage to private organizations.
- “sensitive,” – damage to private organizations
- “public” – Posted posts in company official websites.
Ownership
- Primary information security roles include business or mission owners, data owners, system owners, custodians, and users.
- BUSINESS OR MISSION OWNERS – senior management
- DATA OWNERS – information owner.
- The system owner is a manager who is responsible for the actual computers that house data.
- A custodian provides hands-on protection of assets, such as data.
- Users must follow the rules; they must comply with mandatory policies, procedures, standards, etc.
- Data controllers create and manage sensitive data within an organization.
- Data processors manage data on behalf of data controllers.
- Organizations should collect the minimum amount of sensitive information that is required.
Memory and Remanence
- It is important to understand data remanence when discussing media sanitization and data destruction.
- RAM is volatile memory used to hold instructions and data of currently running programs. It loses integrity after loss of power.
- ROM is nonvolatile; data stored in ROM maintains integrity after loss of power.
- SRAM is fast, expensive memory that uses small latches called “flip-flops” to store bits.
- Flash memory, such as a USB thumb drive.
- programmable read-only memory (PROM),
- erasable programmable read-only memory (EPROM)
- PROM can be written to once, typically at the factory. EPROM and EEPROM may be “flashed,” or erased and written to multiple times.
- A SSD is a combination of flash memory (EEPROM) and
- This issue is called data remanence, referring to “remnants” of data left behind.
- OVERWRITING – Simply “deleting” a file removes the entry from a file allocation table (FAT) and marks the data blocks as “unallocated.” Reformatting a disk destroys the old FAT and replaces it with a new one.
- Degaussing – destroys the integrity of magnetic medium, such as a tape or disk drive.
- Destruction physically destroys the integrity of media by damaging or destroying the media itself, such as the platters of a disk drive.
- SHREDDING: A simple form of media sanitization is shredding, a type of physical destruction.
Data Security Controls
- OCTAVE® stands for Operationally Critical Threat, Asset, and Vulnerability Evaluation, a risk management framework from Carnegie Mellon University. OCTAVE® describes a three-phase process for managing risk.
- Phase 1 identifies staff knowledge, assets, and threats.
- Phase 2 identifies vulnerabilities and evaluates safeguards.
- Phase 3 conducts the risk analysis and develops the risk mitigation strategy.
- The Common Criteria uses specific terms when defining specific portions of the testing process.
- Target of evaluation (ToE): The system or product that is being evaluated
- Security target: The documentation describing the ToE, including the security requirements and
- operational environment
- Protection profile: An independent set of security requirements and objectives for a specific
- category of products or systems, such as firewalls or intrusion detection systems
- Evaluation assurance level (EAL): The evaluation score of the tested product or system
- The Common Criteria levels are
- EAL1: Functionally tested
- EAL2: Structurally tested
- EAL3: Methodically tested and checked
- EAL4: Methodically designed, tested, and reviewed
- EAL5: Semi Formally designed, and tested
- EAL6: Semi Formally verified, designed, and tested
- EAL7: Formally verified, designed, and tested 6.
- ISO 17799 was a broad-based approach for the information security code of practice by the International Organization for Standardization.
- ISO/IEC 17799:2005 Information technology—Security Techniques—Code of Practice for Information Security Management. Changed to ISO 27002 in 2005.
- ISO/IEC 27001:2005 Information technology—Security techniques—Information Security Management Systems—Requirements.
- COBIT is a control framework for employing information security governance best practices within an organization – ISACA.
- ITIL® (Information Technology Infrastructure Library) is a framework for providing best services in IT Service Management
- Tailoring is the process of customizing a standard for an organization.
Destroying Sensitive Data:
- Erasing:Erasing media is simply performing a delete operation against a file, a selection of files, or the entire media.
- Clearing:Clearing, or overwriting, is a process of preparing media for reuse and ensuring that the cleared data cannot be recovered using traditional recovery tools.
- Purging:Purging is a more intense form of clearing that prepares media for reuse in less secure environments. It provides a level of assurance that the original data is not recoverable using any known methods.
- Degaussing: A degausser creates a strong magnetic field that erases data on some media in a process called degaussing. Technicians commonly use degaussing methods to remove data from magnetic tapes with the goal of returning the tape to its original state.
- Destruction:Destruction is the final stage in the life cycle of media and is the most secure method of sanitizing media. When destroying
Security policies, standards & guidelines:
- Policies first and highest level of documentation.
- – Regulatory (required due to laws, regulations, compliance and specific industry standards!)
– Advisory (not mandatory but strongly suggested
– Informative to inform the reader - Standards – Specify use of specific technologies in a uniform way.
- Guidelines – same as standards but not forced to follow.
- Procedures – detailed steps to perform a task.
- Baseline – minimum level of security
- Security planning – involves security scope, providing security management responsibilities and testing security measures for effectiveness.
US-EU (Swiss) Safe Harbor:
- The EU Data Protection Directive To be replaced, in 2018, by the General Data Protection Regulation (GDPR).Bridge differences in approach and provide a streamlined means for U.S. organizations to comply with European Commissions.
XMIND Diagram:

Leave a comment